News
Cloud Computing Thinks Small (and Medium Sized Business)
Posted in: cloud, Cloud Virtualization, Innovation, IT Management, SMB - Jun 05, 2021Cloud computing, the offloading of company data functions to offsite cloud providers, has been hailed as the tool that’s enabled the decentralization of business during the COVID economy. It’s also become utterly mainstream in business, with Cisco reporting that 92 percent of data workloads were handled in 2020 by cloud computing. The same report also showed that the United States led the globe in cloud computing workloads.
How can cloud computing benefit small- to medium-sized business?
If you’re a small- to medium-sized business, you may be wondering how you make the transition to local data operations to the cloud. Is it right for your business? For an increasing number of growing companies, the answer is yes. They’re finding Software as a service (SaaS), data storage solutions, cloud-based security, ERP, customer service, and more can be migrated to the cloud quickly and affordably. As the pace of business continues to quicken, many small businesses are finding that cloud computing offers unprecedented flexibility and efficiencies of scale that can help them achieve their growth goals, for less.
Procoders-Ukraine CEO Oleg Kopachovets works extensively with cloud-based services in his work for overseas clients.
“I often tell clients that using cloud services is a lot like the cost-shifting benefits you get from hiring an IT consulting firm. You shift the cost of your data center, or the software, or the service, or whatever you’re buying from the cloud from being a hard internal cost to a regular, monthly fee.”
“This can be a really wonderful thing for a small to medium sized business,” Kopachovets adds. “You don’t have to worry about the cost of upgrading equipment, or costly updates that create work slowdowns for your staff. There’s a reason why we’ve reached a tipping point for companies migrating their business to the cloud. It’s just good business.”
Advantages of cloud computing in the SMB setting
Lowered equipment costs
What’s cheaper? Purchasing racks of servers or simply paying one monthly subscription fee to put it all in the cloud? For most companies, that’s not hard math. When compared with the cost of handling all IT functions on site, cloud computing nearly always saves a company money. In fact, KPMG reports that most companies they surveyed were saving between 30 to 40 percent as a result of migrating to the cloud.
Less money spent on maintenance
When you offload to the cloud, you offload not just equipment costs, but the costs of employees to run and maintain that equipment. You also reduce the need for the square footage to house, cool and maintain your equipment, too.
Less money spent on software
Software-as-a-Service has become so common most companies aren’t bothering with purchasing user-by-user software packages anymore. When you purchase software (SaaS) services through the cloud, you also offload the service around those programs, and never have to worry about complicated system wide updates. All that is handled for you, automatically.
Improved security and disaster recovery
According to a latest survey by Sophos, the average ransomware attack can cost a company up to $2 million. Despite this liability, the majority (54 percent) of the IT security experts surveyed said their companies didn’t have the inhouse expertise to deal with this kind of high-level security risk.
Offload your data storage and software operations to the cloud reduces your exposure to hackers significantly. After all, it’s a lot harder to hack Amazon or Google than it is an individual company. And when floods, or power outages or wildfires threaten your business, you can rest easy knowing that your cloud-based business can still work, decentralized from your data center. Why not take advantage of the resources the big players can offer your small business?
Unlimited scalability
Perhaps one of the biggest things small businesses struggle with is how to scale up their operations quickly. Making equipment purchases, housing equipment and paying people to keep internal functions running can get expensive quick. Cloud computing eliminates that problem completely, allowing you to purchase what you need, and only what you need, for a simple flat fee. And if you pivot your business plan, no worries. You can drop whatever services you’re using and move onto the next one.
Planning your migration
Whether you are integrating software as a service, platform as a service, infrastructure as a service or security as a service, the decision to invest in cloud computing may have to do with the cost of making the migration.
“When you’re bringing in cloud computing, the first consideration a business must take is an inventory of all the applications they use—everything that a CEO uses to the time keeping software the receptionist might be using,” said Sitima Fowler, partner at national IT services firm Iconic IT.
“Migration is a process.”
“Then an evaluation should be done to determine whether these applications can run in the cloud optimally. Chances are, not everything can be move to the cloud at once. It’s a journey and we generally to do it one by one, starting with the main line of business software and email. After that we implement a central identity management system to authenticate every user. We give them access to only to the applications they need to get their job done, optimizing the process for how users work and their respective security levels. Migration is a process.”
Listen up: To dive deeper into trends surrounding cloud computing hear what other IT leaders are doing in the cloud in 2021 with this recent Datamation podcast.
The post Cloud Computing Thinks Small (and Medium Sized Business) appeared first on CIO Insight.
topYou Really Can’t Do Enough Security Training
Posted in: Security, training - Jun 04, 2021When it comes to security training in the era of near-daily phishing and ransomware attacks, can your company ever be over-prepared?
Solution spending grows, but investment in people must as well.
Organizations spend a huge amount on security these days. Some large banks, for example, are now allocating as much as a billion dollars annually on cybersecurity – and two thirds of finance executives expect cybersecurity budgets to keep rising. The economics behind it are simple. Cybercrime is costs more than $3 trillion a year and that amount is expected to double in 2021. But much of this money goes on technology and implementation.
Not nearly enough is directed toward the people and process side. Security training in particular is an area in need of improvement according to a new report by Computer Economics on Security Training Adoption and Best Practices 2021.
Security training certainly needs to improve how it accomplishes the in-depth and continuing training of IT personnel. It isn’t enough to train and update IT security staff. All of IT, and very definitely including developers, must become well-versed in security threats and technologies.
But perhaps the biggest weakness is how organizations address the issue of ensuring that all personnel become well-trained in security. In an era of phishing and ransomware, you really can’t do enough security training of general personnel.
Policy education alone is not enough.
In some companies, the security training given to staff only goes as far as insisting all users sign off on reading organizational security policies and procedures. But how much of it are they likely to retain? It is one thing to devise robust security policies and another thing to have them applied. Policy is of little value if IT personnel and users violate them or fail to be diligent in their application.
The Computer Economics report emphasizes that sound security policies must be supported by formal and consistent training of staff. They must become knowledgeable on the various threats they face, how to respond, and how to avoid being fooled by the latest phishing or social engineering ruse. They must understand that short cuts that circumvent security policies invite danger.
Recent ransomware scares have emphasized the need for heightened security. But Computer Economics surveys reveal that too few organizations consistently and formally conduct security training. What this means, in effect, is that many organizations may have implemented some form of security training. But it is often doing it in a haphazard or hit-and-miss fashion. The report calls for organizations to evaluate existing training programs to determine where they can be improved. By raising the quality and comprehensiveness of security training initiatives, the number of breaches and attacks can be decreased.
Security training strengthens the human firewall.
Security training can help establish what might be considered a human firewall i.e. every employee is sufficiently clued in that they are actively on the alert for attacks, know when they face suspicious traffic, and apply peer pressure to knock out any sloppy security behavior they see around them. They realize that one inattentive person is all it takes to open the door to online predators.
The face that the Computer Economics survey found that 86% of companies performing security training in 2020 stands in sharp counterpoint to the alarming rise in the number of security breaches of late. It takes more than technology to thwart cybercriminals and it is this human factor that must be addressed more forcefully via training.
It isn’t hard to train personnel into a greater awareness of the threats they face. Read them in on the various forms of phishing and the other insidious practices employed by cybercriminals. And keep reading them in until IT no longer has to put out phishing fires on a regular basis. Companies such as Living Security and KnowBe4 offer programs that can set organizations on the road to heightened security via the building of a human firewall.
Next-generation firewalls not withstanding, the weakest point in your security infrastructure is invariably going to be your people. While your company may conduct a fire drill every year, a data breach is a much more likely scenario than a four-alarm blaze. Which is why frequent security training needs to be a frequent enterprise-wide undertaking.
The post You Really Can’t Do Enough Security Training appeared first on CIO Insight.
topAre Air Gapped Networks Secure?
Posted in: air gap, air gapped, air gapped network, air-gapped systems, colonial pipeline hack, cybersecurity, Infrastructure, IT Management, malware, network audit, network infrastructure, network security, Security, security breach, Stuxnet, Stuxnet worm - Jun 04, 2021Ours is a deeply interwoven and breachable world, which often means trouble for enterprise security. According to IBM’s 2020 Cost of a Data Breach Report, the average cyberattack costs a business $3.86 million, and the United States’ average cost per breach has reached $8.6 million. There is some good news though: businesses that are investing in better network security infrastructure and policies, such as incident response and security automation, are saving anywhere from $2 million to $3.58 million when a breach does occur. Although it won’t work for every business model, air gapped networks can provide one of the highest levels of security to enterprise infrastructure when they are managed closely, stopping many potential breaches in their tracks.
Readers also Read: End-to-End Encryption: Important Pros and Cons
Taking a Look at Air Gapped Networks
- What is an Air Gapped Network?
- How Do You Air Gap a Computer?
- How Secure are Air Gapped Networks?
- Why Air Gapped Networks are Important
What is an Air Gapped Network?
An air gapped network is a network that has been separated from other public and private networks with an effective “gap of air.” This means that the air gapped network is disconnected from the public internet, external email, and any other ways of directly communicating from one network to another.
Consider this visual: if two mountains are separated by a valley, the only way to make it to the other mountain is via a direct path or form of transportation, which could be anything from a bridge to a helicopter that will fly you over there. The bridges and helicopters in this scenario exemplify the external network connections, like public network access and email messages, that make it easier for hackers to latch onto and gain access to a private network.
But let’s say that these two mountains are in a highly isolated part of the world and there’s no form of transportation or other access to cross between the mountains. The valley between them is a gap of air, one that few travelers will want to take the time and risk to traverse. In the same way, adding a gap of air between your private network and other public networks wards off most attacks because the attack vector has been complicated through isolation.
Data movement in an air gapped network can only happen via external, non-network means: removable hardware or media like a USB drive can be used to transfer information in and out of an air-gapped network, and transient devices like laptops can be authorized to connect to the air gapped network, though with very specific permissions. Think of these as hidden paths or special access transportation that only authorized travelers can use to access your air gapped network. But these require a human with physical access to both machines, along with proper authentication credentials.
More on Enterprise Networks: Understanding VPNs: The Pros and Cons of IPSec and SSL
How Do You Air Gap a Computer?
Air gapped computers closely resemble air gapped networks, but they’re more focused on the device and personal use levels. The idea is to disconnect the individual device from any outside networks or information, and it can be used for reasons ranging from increased personal privacy to improved performance of non-network applications.
In order to air gap a computer, you’ll need to completely disconnect it from everything else. That means disabling WiFi and Bluetooth, disconnecting from the ethernet cable, and double checking that no other forms of communication or data transference are available. Air gapping a computer involves disconnecting cables and disabling all network hardware.
How to Stay Secure When You Can’t Air Gap: VPN vs. SDP vs. ZTNA: Who Won 2020?
How Secure are Air Gapped Networks?
Air gapped networks theoretically make up one of the highest forms of network security, because the increased levels of isolation make it difficult for information to be accidentally or purposely moved to and from that network. Most hackers only have the skill level or patience to perform a network-level attack from a distance, but air gapping almost necessitates that they gain direct in-person access to a network device. They cannot simply hop over from another network or get logins through phishing communications, so most malicious actors will stop before they ever breach your network.
However, there are valid and proven concerns about the actual physical security of air gapped networks, namely the transient devices that are allowed to connect to it. Who’s to say what happens to a USB drive or laptop before, during, and after its time connected to an air gapped network? What if an authorized user accidentally or purposely uses this hardware to carry information (or malware) to and from the network? The Stuxnet worm case from 2010 is a strong example of how network hardware can cause damage, as that particular strain of malware spread to Iranian industrial and nuclear plants via USB drives.
Network Policies to Secure Air Gapped Networks
Ultimately, air gapped networks are only as secure as your networking and security policies are willing and able to make them. They can be nearly foolproof if strict network policies are put in place and constantly overseen by network administrators. Consistent monitoring should especially be applied to removable media, transient devices like laptops and computers, modems, and VPNs.
Here are just a few steps that your network administrators should take to make their air gapped networks as secure as possible:
- Enforce strict policies about where air gapped network hardware can physically go, who can use it outside of designated physical areas, and how it can be used. It’s a good idea to limit these devices to upper-level management, power users, and anyone else who absolutely needs that level of access.
- Invest in strong network monitoring practices and tools so that you can immediately catch users and devices if they overstep in data access and sharing privileges.
- Develop a detailed network audit checklist that can help you to set and enforce policies for both devices and users on the network.
Why Air Gapped Networks are Important
Although there are some doubts about how effective air gapped networks currently are and how effective they’ll be as the growth of AI and IoT devices necessitates always-on communication between private and public networks, there are still many security and workflow advantages to be found in an air gapped network:
- Air gapped networks increase isolation and secrecy, thus increasing security in high risk scenarios and industries (i.e. government, military, etc.).
- You can easily protect and separate your highly secure programs that don’t need constant network access.
- Remote hacking is nearly impossible; you have to be onsite, which makes it more difficult for hackers to gain access.
- Payment and control systems can be kept separate from the rest of the public or private network(s) that your business uses.
In a world where security breaches are costing businesses millions of dollars every year and major security breaches hit the news on an almost weekly basis, air gapping your network is one of many choices you have to protect your data and users from a growing number of malicious actors.
Security Measures that Can Prevent Cyber Attacks: What Lessons Can CIOs Learn from the Colonial Pipeline Hack?
The post Are Air Gapped Networks Secure? appeared first on CIO Insight.
topCan Gamification Drive Employee Retention?
Posted in: gamification, gamification tools, IT Strategy - Jun 03, 2021
Employee turnover costs employers more than $630 billion annually, according to The Work Institute’s 2020 Retention Report. While CIOs search for solutions for retaining great employees and keeping their companies successful, gamification may offer concrete strategies that can show measurable results.
Gamification is sometimes oversimplified as reimagining one’s mundane tasks as fun goals or exciting challenges. However, in addition to making daily work more entertaining, gamifying work encourages engagement in activities and improves the memories of those participating.
Is Gamification the Right Step?
The 2020 Retention Report notes the drive for career development caused 20 out of 100 employees to quit in 2019. The report separately states that “Career Development has been the #1 Category for ten straight years,” and that the opportunity to advance would have kept them with the company.
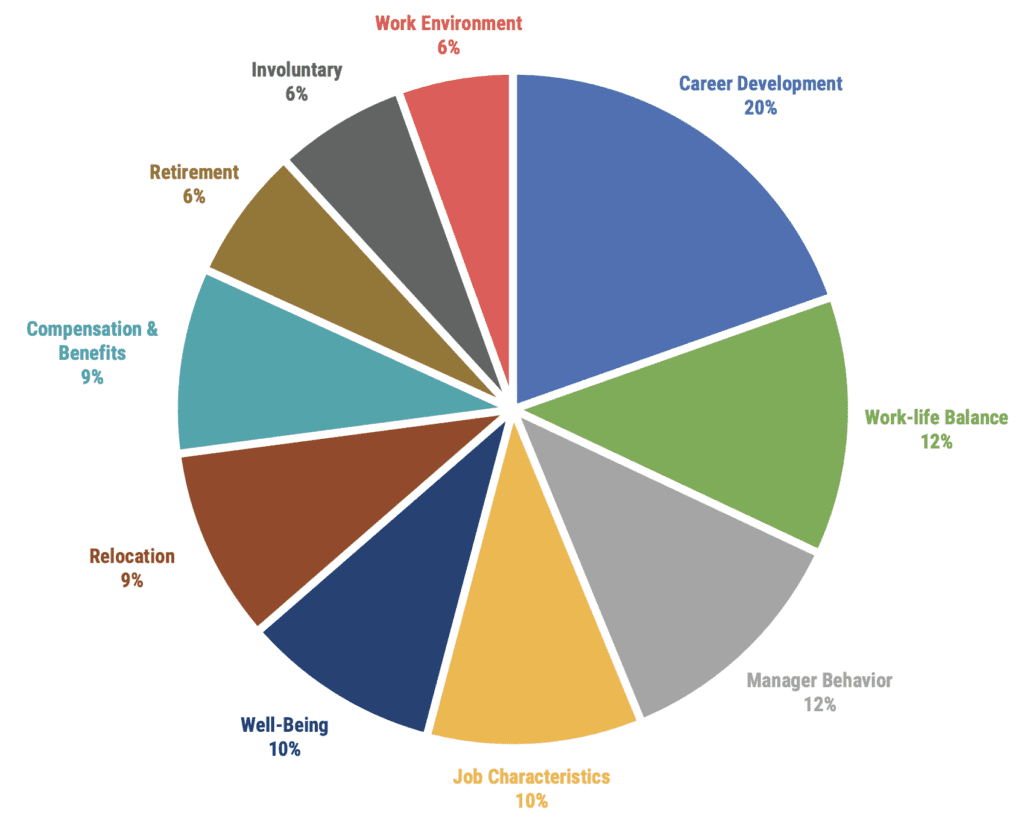
Considering the primary importance of career development in retention, gamification can play a critical and cost-effective role in connecting employees with the skills and industry knowledge they need to excel within the company and their career fields.
Gamification and upskilling
TELUS International’s CIO Michael Ringman points to gamification as the key to quickly and effectively upskilling employees.
“The various learning programs we offer, such as our Global Language Academy and MyGrowth are offered virtually and in many cases are accessible on mobile devices to enable our global team to access them from anywhere at any time.”
“By evolving words on a page into engaging, multi-sensory experiences such as simulations, virtual role playing and leaderboard scoring, gamification encourages employees to complete training modules more quickly while also gaining a deeper understanding of the subject matter by experiencing it at their own pace and in a more immersive fashion.
“When we allocate badges as rewards, give employees the ability to create their own avatars, and provide real-time visualized progress bars, we have seen impactful boosts in engagement and productivity that ultimately drive career progression and employee retention.”
“In 2020, we achieved world-class employee engagement scores of 86% and continue to consistently achieve 50% lower attrition rates vs. our competitors.”
“Gamification is an important factor for employee retention in the digital environment, where they earn points, status, and rewards as they improve their skills to achieve company goals and objectives,” says Caroline Lee, co-founder of CocoSign. On-the-spot learning is a powerful tool used to “make the workplace more exciting and increase employee retention.” And gamifying employee retention can be broadened through a whole structure, or tailored to improve a specific department.
Managing a team of 70 software designers and engineers, ISBX president Arthur Iinuma says that interactive leaderboards create friendly competition in his company to “increase employee productivity and foster more engagement in the workplace.”
“We have found that gamification has incentivized problem-solving in terms of developing new products and meeting customers’ needs. Gamification has offered intellectual stimulation, encouraging increased employee engagement and performance. Team-based gamification has forged stronger bonds between team members.” Iinuma estimates overall productivity has increased “in the region of 20 percent due to gamification.”
Gamification and retirement savings
“Our employees are an extended family, and we want to do as much as we can to retain them,” said Bruce Watkins, founder and CEO of Cal Preserving, Inc.
“We previously offered our employees a 401k plan. We found the experience was horrible because of the complexity of administering it. So we recently moved to a new provider, Xiggit. It’s a low-cost, simple web-based IRA program that handles the ongoing retirement savings administration for us.
“We didn’t set out to offer any gamification to retain employees but the app has a gamified tool (Learn ‘n Earn) that informs employees about our company’s benefits and improves their financial knowledge. They earn a little in the daily game but, more importantly, it’s improved their money habits.
“Some employees can’t believe how much money they’ve saved in such a short period of time. Our workers feel differently about our company because of these benefits and their financial stress is lower. We know that employee retention will improve.”
Any CIO mulling some sort of gamifying strategy should make sure that they ask the right questions: Does this new approach prompt greater yields in employees? Does the gamified aspect reduce training and upskilling to a relentless slog to beat a point system?
To be a worthwhile return on investment, gamification must grow the team member’s overall skill set, in a way that is both engaging and that leads to enhanced job satisfaction.
The post Can Gamification Drive Employee Retention? appeared first on CIO Insight.
topEnd-to-End Encryption: Important Pros and Cons
Posted in: Big Data, Mobile, Security - Jun 02, 2021According to the 2020 Cost of a Data Breach Report by Ponemon Institute and IBM Security, data breaches are costing enterprises $3.86 million on average, and they’re taking an average of 280 days to discover the problem. Clearly, hackers can and already do easily identify and access both corporate and personal information when files are transmitted from device to device unless certain cybersecurity measures are put into place. End-to-end encryption is the easiest solution for protecting this data so it doesn’t get into the wrong hands.
End-to-end encryption is the practice of encrypting data and information as it passes from device to device. The sending and receiving devices can see the original contents, but no other interceptors have the correct keys to decrypt the message. This approach to cybersecurity offers many benefits to companies and users that implement the protection, but there are still some drawbacks in areas like consumer-provider relationships. Read on to learn more about how end-to-end encryption works, as well as some of the pros and cons of end-to-end encryption security.
“The total number of records compromised in 2020 exceeded 37 billion, a 141% increase compared to 2019 and by far the most records exposed in a single year since we have been reporting on data breach activity.” –Risk Based Security 2020 Year End Report
Read Next: 2021’s Most Successful Phishing Ploys (So Far)
What is End-to-End Encryption?
- How it Works
- The Pros of End-to-End Encryption
- The Cons of End-to-End Encryption
- Apps & Software that Use End-to-End Encryption
How it Works
But how does end-to-end encryption keep data encrypted while it travels? Two cryptographic keys, a public key and a private key, are generated on the sender’s device. The public key is public, in the sense that a public key can be generated by anyone.
However, the paired private key can only be generated by that particular sender and can only be used to decrypt data for the designated recipient device. Hackers can theoretically intercept the message in transit and service providers can access the encrypted message in order to store it, but it will remain completely illegible until it is received and decrypted by the recipient device. This practice ensures that the data can only be viewed in its true form on the sending and receiving devices, and nowhere in between.When end-to-end encryption is applied to data in transit, the data is first encrypted, or jumbled, on the sending device. The message cannot be decrypted by hackers, service providers, or anyone else until it is received by the end device.
The Pros of End-to-End Encryption
Protection of Privacy
With end-to-end encryption, private communications and other details, like timestamps and significant locations, are not easily read if intercepted by hackers or service providers like Google or Apple. When end-to-end encryption is enabled, you can rest assured that personal privacy prevails and consumer data is protected from outside viewers.
Integrity of Data
In other security setups, outside users can potentially gain access to a piece of data and manipulate its contents before it reaches the recipient (or worse, they can stop its delivery entirely). End-to-end encryption means that these malicious actors do not have the necessary key to access data in transit, so the integrity of data is maintained.
Highly Sensitive Data Exchanges
Whether it’s due diligence for a high-profile M&A transaction or the sharing of sensitive government intelligence data, end-to-end encryption is one solution that makes sure that no one outside of the sending and receiving parties can spread highly sensitive information. The reasons are twofold: 1) The key system in end-to-end encryption prevents unauthorized devices from opening the message. 2) If users maliciously or accidentally come across the message, end-to-end encryption has made it indecipherable to them.
Device Level Over Server Level
Other types of encryption focus on encrypting data at the server level, but if a malicious actor or other outsider gains access to that server, they can decrypt any information in that server fairly easily. Overcoming end-to-end encryption requires hackers to perform device-level hacks to get the information that they want, which is considerably more difficult and time-consuming to do, leading most hackers to avoid those types of attacks altogether.
Avoiding High-Cost Attacks and Reputation Damage
Let’s take a look at the biggest data breach in history: Yahoo’s 2013 breach that compromised approximately 3 billion user accounts (all of their customers’ accounts at that time). Yahoo claims that no clear-text passwords or financial information were compromised in the attack, but experts believe that Yahoo’s “outdated, easy-to-crack” encryption still exposed those records—billions of records—to malicious actors.
Needless to say, this attack damaged Yahoo’s reputation with customers, but it also damaged their negotiation powers with other major businesses. In 2017, Yahoo was in acquisition negotiations with Verizon, and after this news came to light, they were forced to lower the price of their assets by at least $350 million.
Making Security Affordable: 8 Low-Cost Ways to Improve Cybersecurity
The Cons of End-to-End Encryption
Although end-to-end encryption offers many high-value benefits to enterprises and users, the security practice still suffers from several shortcomings and has led to some public safety concerns:
Ledger is Still Available
End-to-end encryption jumbles all of your data’s contents in transit, but it does not hide the fact that data is being transferred. The ledger of communication remains, so people can still find records of transactions and possibly deduce the contents, based on sending and receiving parties.
Unreliable Receiving Devices
End-to-end encryption does not guarantee the protection of data once it reaches the receiving device. If there’s a security problem on that device or if that device falls into the wrong hands, the data has already been decrypted on the receiving device, leaving it susceptible to outside parties who gain access to the device.
Law Enforcement and Surveillance Concerns
One of the most important and highly controversial issues with end-to-end encryption is that it’s almost too successful at protecting data from third parties. This is a great feature as far as protecting private information against hackers, but what about for law enforcement and intelligence officers who need to conduct a serious investigation?
With end-to-end encryption, they cannot access evidence that has been encrypted, and neither can service providers if they are asked to cooperate in the investigation. Only participating devices can provide the information they need. In serious cases related to allegations like terrorism, murder, and physical abuse, this data protection becomes a major hindrance to public safety and national security.
Many national governments and international committees have fought against end-to-end encryption in personal devices and applications for this reason. One of the most recent end-to-end encryption ban coalitions includes India, Japan, New Zealand, Australia, the UK, and the United States. In their International Statement on End-to-End Encryption and Public Safety on October 11, 2020, they called for a ban on end-to-end encryption in apps like WhatsApp and pushed for technology companies to allow greater data access to international law enforcement forces.
Learn More About Security at CISA: Cyber Agency Launches Security Awareness Campaign
Apps & Software that Use End-to-End Encryption
Several major companies have added end-to-end encryption features to their offerings over the years, and while some have experienced great success, others have become embroiled in controversy.
| Zoom | -Arrived in late October 2020 as a technical preview for free and paid users -Zoom's traditional GCM encryption remains, but with public key cryptography and meeting participant key distribution -Users can enable on meetings so that only participants have the decryption key (not even Zoom servers have access with this approach) -Users can confirm that they are using end-to-end encryption by looking for a green shield on their Zoom window -In November 2020, Zoom came to a settlement with the FTC regarding allegations that they had misled customers into thinking they offered end-to-end encryption since 2016. Their previous “end-to-end, 256-bit encryption” still gave Zoom full access to meeting data. |
| Whatsapp/Facebook | -End-to-end encryption fully launched in April 2016 -Designed to secure messages, photos, videos, voice messages, documents, status updates, and calls -Whatsapp changed its privacy policy in early 2021, now allowing it to share metadata on users with Facebook, its parent company -Millions of users moved away from Whatsapp after finding out how their metadata could be used |
| Amazon Ring | -Video end-to-end encryption launched in January 2021 -Only enrolled customer mobile devices can decrypt security footage -Launched in response to several security breaches and concerns in previous years |
| Microsoft Teams | -Announced end-to-end encryption plans at Ignite conference in March 2021 -Functionality is expected for both personal and business use cases, on Signal, Skype, Jabber, and Teams -Expected to secure 1:1 meetings and communications between users on Microsoft Teams |
Data breaches are costing enterprises around $3.86 million per year, and that number only seems to grow, particularly in key areas of infrastructure. Although there’s some controversy and concerns surrounding how end-to-end encryption works, it’s clear that the solution is a valuable security investment for the enterprises that select it and the consumers who benefit from it.
More on End-to-End Encryption from IT Business Edge: Enterprise End-to-End Encryption is on the Rise
The post End-to-End Encryption: Important Pros and Cons appeared first on CIO Insight.
topDaman News and Events
This showcases our company news and upcoming events. Please check back as this page will change frequently.


