News
Edge Computing vs Fog Computing: What’s the Difference?
Posted in: edge computing, edge computing companies, edge data center, edge of network, fog computing, Infrastructure - Sep 28, 2021Edge computing vs fog computing is becoming a frequent discussion as cloud computing gains popularity and people rely on more Internet of Things (IoT) devices. Both technologies have significantly changed IoT data processing possibilities for cloud computing clients.
Here’s an explanation of how edge and fog computing differ, and how they complement each other.
Read more: Top Edge Computing Companies for 2021
What Is the Difference Between Edge Computing and Fog Computing?
Edge computing and fog computing allow processing data within a local network rather than sending it to the cloud. That benefit decreases latency and increases security. The main difference between the two is processing location.
With edge computing, data processing typically occurs directly on a sensor-equipped product that collects the information or a gateway device physically close to those sensors.
Fog computing moves edge computing activities to LAN hardware or processors connected to it.
Fog computing moves edge computing activities to local area network (LAN) hardware or processors connected to it. These may be physically farther from the data-capturing sensors compared to edge computing.
Jessica Califano, head of marketing and communications at Temboo, clarified, “Fog computing and edge computing are effectively the same thing. Both are concerned with leveraging the computing capabilities within a local network to carry out computation tasks that would ordinarily have been carried out in the cloud.”
It’ll also soon become clear that the most important determination in the edge computing vs fog computing debate is usually not which one is “better.” Ideally, decision-makers should understand what works best for their applications and business structures.
How Do Edge and Fog Computing Make IoT Data Processing More Secure?
As people become more reliant on IoT data and cloud computing, they’re often increasingly aware of the need to keep information as secure as possible — due to what hackers could achieve by exploiting it.
For example, if a manufacturer’s IoT data is stolen, cybercriminals could learn proprietary details about that organization’s production methods.
Read more: Top Cyber Security Threats to Organizations
Keeping Data Moving
Sending data over long distances to the cloud increases the chances of hackers intercepting the data before it arrives at that destination. Cybersecurity expert John Arquilla recently said, “I have a very simple mantra worth remembering: Data at rest are data at risk.” He also confirmed that the location makes a significant difference when people want to keep critical information safe.
“Where should information go to be safe? The best places are in the cloud and ‘the fog.’ Cloud computing is about putting data on someone else’s system, and it is a practice on the rise. Growing comfort with the cloud should encourage a willingness to put even the most sensitive information out on it,” he noted.
‘Data at rest are data at risk.’
Arquilla continued, “The fog is a form of edge computing and consists of those structures between systems that produce data and the cloud. Because it is outside the servers in one’s own data center, the fog offers yet another hiding and storage space that hackers will find hard to access. Both are far better than simply keeping key information close.” Fog computing does not eliminate IoT security risks, but it minimizes them.
Shortening the overall travel time with edge and fog computing makes IoT workload handling safer. However, as Arquilla discussed, edge and fog computing support data decentralization, keeping the information safer.
Making Smarter Data Processing Choices
Fog computing operates within the cloud rather than outside of it. Thus, people may use it to monitor smaller IoT devices that do not have built-in security measures.
It’s also possible to rely on fog computing to simultaneously update IoT devices without requiring they first connect to the cloud. Doing that could keep the respective devices more secure. Another way to protect fog computing is to install virtual firewalls around it.
The rise of the IoT and cloud computing has spurred a related interest in serverless computing. It’s a highly scalable process that tasks cloud providers with all servers and associated management tasks, freeing companies from having on-premise equipment.
Just as there are security risks with sending all data to the cloud, the same is true with processing everything at the edge.
That approach makes sense for many organizations. However, it takes substantial time and effort to design a serverless architecture that performs well and is easily maintained. In most cases, the ideal approach is to decide what data to process in the cloud and what’s better suited for edge and fog computing.
Just as there are security risks with sending all data to the cloud, the same is true with processing everything at the edge. Cloud providers have stringent security protocols that collectively reduce cyberattack risks. It’s not always possible to apply similar measures to edge devices.
Fog and edge computing let service providers filter out sensitive data to be processed locally while handling nonsensitive information in the cloud. That’s useful for industries like health care and retail, which often deal with personal data.
Some applications also demand local data processing to function correctly. For example, the information handling associated with smart assistants often happens directly on the devices. That’s the optimal choice, since people expect prompt answers to their queries.
Read more: Edge Computing Trends in 2021
What Does the Future Hold for Fog and Edge Computing?
Most edge and fog computing use cases relate to the Internet of Things. That’s probably because most research on the matter has so far centered on IoT possibilities. However, that could change as people get more curious about exploring past perceived limits. For example, research from Wayne State University suggests it could improve firefighting.
When crews have accurate, current details before and while fighting a blaze, they’re more likely to succeed in getting it under control, saving lives and preserving property. The research indicated that processing relevant data on a firetruck or within a localized data center could provide the faster speeds necessary when dealing with critical details.
Edge and fog computing could also prove useful for handling the massive amounts of data captured by video cameras at live sporting events. One high-definition camera can generate about 1.8 GB of data each hour, depending on its settings. Processing this information locally — rather than transferring it to the cloud — could improve the experiences of people watching high-profile events, such as the Olympics and the Super Bowl.
Edge Computing vs Fog Computing: Supporting Tech Advancements
As people learn more about edge and fog computing, they’ll achieve a more balanced perspective by not trying to figure out which technology brings superior offerings.
In most cases, these technologies complement each other. Fog and edge computing will push technology and its applications forward for the foreseeable future, particularly when the people using them take the time to understand the advantages they bring.
Read next: Edge Computing: Tips for Hiring and Getting Hired
The post Edge Computing vs Fog Computing: What’s the Difference? appeared first on CIO Insight.
topThe Information Gap: How to Keep Bad Analytics from Bringing Down Your Business
Posted in: Business Intelligence - Sep 24, 2021During this presentation, we will review the common causes of the information gap as companies undertake a data and analytics initiative. We'll explore the most common obstacles associated with delivering data and analytics to a business audience, the warning signs that your organization may have an information gap, and how successful companies bridge that gap.top
Top Cloud Computing Companies for 2021
Posted in: Adobe, artificial intelligence, AWS, Cisco, cloud companies, cloud computing, cloud security, Cloud Storage, Cloud Virtualization, Enterprise Apps, Google Cloud, HPE GreenLake, IaaS, IBM cloud, Infrastructure, infrastructure-as-a-service, IoT, IT Management, IT Strategy, machine learning, Microsoft Azure, Oracle Cloud, PaaS, platform-as-a-service, SaaS, Salesforce, Security, software-as-a-service, top cloud companies, VMware Cloud - Sep 23, 2021Companies around the globe have been talking about digital transformation for years, but with the entrance of the COVID-19 pandemic and new workplace challenges, most enterprises have necessarily sped up their tech modernization efforts. Hybrid cloud, multicloud, and cloud computing companies and services have recognized this digital transformation push and are providing a wider range of cloud services accordingly.
Advancing a strategy in cloud computing — or making computing capabilities available over the internet and distributed virtual data centers rather than on-premises data centers — is one of the top priorities for most organizations today. The data reflects this: according to a study from Fortune Business Insights, the global cloud computing market hit $250 billion in 2021 and is expected to reach $791.5 billion by 2028.
Some of this growth comes from new challenges found in a distributed global workforce, but exciting changes in machine learning (ML), artificial intelligence (AI), Internet of Things (IoT), and big data growth have also precipitated the cloud’s expansion. Learn more about how the top cloud computing companies are providing the solutions that meet ever-changing business operation needs at scale.
Also Read: How COVID-19 Is Driving Digital Transformation
A Closer Look at the Best Cloud Computing Solutions
- What Do Cloud Companies Do?
- Top Cloud Companies on the Market
- Key Features From Cloud Vendors
- Tips for Choosing a Cloud Vendor
- Who Needs Cloud Solutions?
What Do Cloud Computing Companies Do?
Cloud computing companies offer a variety of enterprise cloud solutions, focused on infrastructure, platform, and/or software-based solutions. Although most smaller cloud companies specialize in one core area of cloud support, the biggest solutions providers tend to specialize in all three key areas of cloud computing services:
SaaS (Software-as-a-Service)
SaaS is a type of solution in which a third-party vendor delivers cloud applications over the internet. They are typically hosted on a remote server and do not require enterprise customers to manage the hardware or software updates involved.
Examples: Google Workspace, Zoom, Dropbox, Slack, HubSpot, Salesforce, ZenDesk
PaaS (Platform-as-a-Service)
In PaaS, the cloud vendor provides enterprises with a cloud platform for application creation and development. With the platform approach, developers can focus on applications while other users or a third party separately manage servers, storage, and other networking features.
Examples: SAP Cloud, AWS Lambda, IBM Cloud Foundry, Red Hat OpenShift, Zoho Creator, Apache Stratos, Magento Commerce
IaaS (Infrastructure-as-a-Service)
IaaS is cloud-based infrastructural support delivered via virtualization technologies. With IaaS, enterprise customers receive self-service compute resources, such as servers, operating systems, and storage — all of which they can scale up or down as needed. Many IaaS solutions offer PaaS and SaaS solutions within their portfolios.
Examples: AWS, Microsoft Azure, Google Cloud, Oracle Cloud, IBM Cloud, Alibaba Cloud, Open Cloud by RackSpace
Top Cloud Companies on the Market
AWS
Best for Public Cloud, Largest Portfolio of Cloud Solutions
AWS is the largest and most widely recognized cloud vendor on the market, providing an IaaS solution with several PaaS and SaaS solutions also in its arsenal. Amazon’s cloud specialties run the gamut of cloud expectations, ranging from storage and container management to compute and virtualization to the management of new technologies powered by AI, ML, and IoT.
AWS is perhaps not the strongest solution for enterprises that want a slower migration or prefer to keep some of their legacy systems on-premises; many enterprises opt for competitors like Microsoft Azure, which are already familiar with traditional on-premises technology management.
However, AWS is making great strides in the area of migration support, offering VMware Cloud on AWS as a virtualization solution for companies needing a more concrete bridge between their traditional data centers and their new cloud infrastructure.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- EC2 virtual cloud servers
- Simple Storage Service (S3) for scalable cloud storage
- RDS, Aurora, and DynamoDB for managed (relational) databases
- SageMaker for building and deploying ML models
- Outposts for running AWS infrastructure on-premises
Microsoft Azure
Best for Hybrid Cloud and Enterprise Interoperability
Microsoft Azure is the second largest public cloud provider and is growing at a quick enough rate that it could eventually surpass AWS. Much of Azure’s success is owed to Microsoft’s longstanding relationships with enterprises and its experience with providing widely used operating systems, applications, and collaborative tools to businesses.
Microsoft’s knowledge of traditional business tools has made Azure a particularly strong resource for organizations that either want to maintain their on-premises infrastructure or plan for a slow transition to the cloud. With hybrid cloud solutions such as Azure Arc, Azure Stack, and Azure Active Directory, customers are provided with several different tools to connect their on-premises infrastructure to the cloud.
Azure also shines in the area of SaaS, turning many of its more traditional product offerings into cloud-friendly applications, such as its CRM and ERP solution, Microsoft Dynamics 365.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- Azure SQL and Azure Cosmos DB for database management
- Virtual Machines
- Virtual Desktop
- Azure Cognitive Services
- Azure Arc
Google Cloud
Best AI/ML Capabilities
The Google Cloud platform is the third largest in terms of revenue, and although it isn’t quite competitive with either AWS or Azure, it is growing quickly, especially for niche markets and use cases. Many of its customers are particularly impressed with its investment in AI and ML technology.
It offers a variety of tools in the AI/ML category, ranging from applications that allow users to train and manage deep learning and ML models, to applications that allow them to analyze emotion, text, and unstructured data like sound.
Google Cloud offers a well-rounded portfolio of other IaaS, PaaS, and SaaS features, but because of Google’s veteran knowledge of networking and search data, it is also one of the top solutions for organizations that want robust analytics in their cloud platform.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- Compute Engine virtual machines
- Cloud Storage for secure, stable object storage
- Cloud SDK command line tools and libraries
- BigQuery data warehouse
- Anthos control plane for application management
IBM Cloud
Best for Multicloud Development
Although IBM Cloud is a much smaller solution than the previous “Big Three,” its portfolio covers the same basics as most other IaaS vendors and especially stands out in the area of multicloud development. Its primary multicloud tool, IBM Cloud Satellite, is labeled as a “managed distributed cloud solution” that helps enterprise users to deploy and manage applications across edge, on-premises, and public cloud environments — regardless of vendor.
Few other cloud platforms have fully tapped into the multicloud space, due to the difficulty of managing differently designed environments, but IBM Cloud Satellite is an IBM investment that delivers cloud services, regulatory and policy features, APIs, and security controls across disparate operational infrastructures.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- Cloud Satellite for multicloud development
- Cloud Block Storage
- Watson AI tools
- Cloud Pak for automation
- Cloud Monitoring for network security monitoring
Oracle Cloud
Best for Embedded Database Software
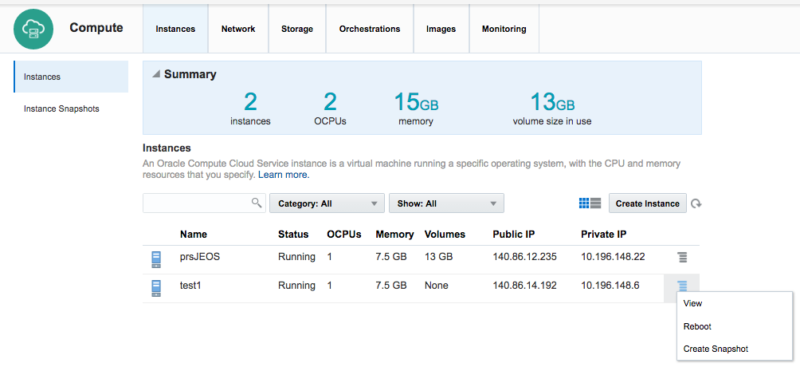
Oracle is best known for the variety of database platforms and services that it offers to enterprise customers. But because of its data management background, Oracle Cloud particularly excels in helping cloud customers organize and manage their data.
One of the top data management tools provided natively within Oracle Cloud is the Oracle Autonomous Database, a unified database that uses ML and other self-healing techniques to automate database management across the cloud.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- Embedded Oracle Autonomous Database solution
- Delivery of bare-metal compute services and network traffic isolation
- Public cloud and edge deployments available
- AI/ML-powered analytics
- Security, identity and access management (IAM), and other compliance-based tools
VMware Cloud
Best for Virtualization and Containerization
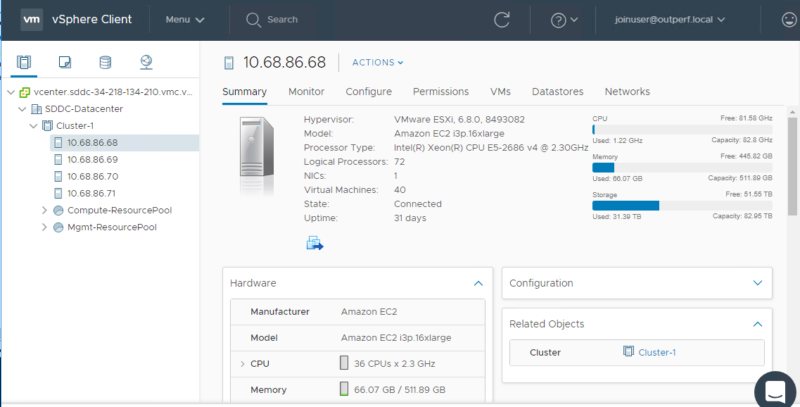
If VMware were a student in middle school gym class, every captain would try to pick them for their dodgeball team. That is to say, VMware is the virtualization engine that assists many of the other top players on this list with its hybrid cloud development, workload migration, and on-premises legacy tool strategies.
Specifically through its relationship with AWS, enterprises can use VMware Tanzu to build, run, and manage applications through Kubernetes-orchestrated containers. Although its core offerings don’t cover the same scope as some of the other IaaS and PaaS competitors, its relationships and the flexibility offered by its containerization technologies give users most of the key tools they’ll need to get started on the cloud.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- VMware Cloud on AWS
- Tanzu for container management
- Cloud Disaster Recovery
- VMware Cloud on Dell EMC
- VMware Cloud Foundation
Salesforce
Best for Customer Relationship Management

Although it does not offer the full spectrum of solutions that many of the other vendors on this list offer, Salesforce is a top contender in its specialty area of customer relationship management (CRM) software.
Its platform is highly scalable, allowing you to add the Service, Marketing, and Sales features as separate or integrated clouds that can scale up or down over time. And with its integration with tools like Slack, Salesforce is also a great solution for keeping users at all levels of a business connected through communication.
Cloud Category: PaaS and SaaS
Key Features:
- Contact, opportunity, and lead management software
- Pipelines, forecasting, reports, and dashboards
- Einstein AI-powered customer service platform
- Email and digital marketing, demand generation, digital advertising, and marketing analytics
- MuleSoft Anypoint Platform for data integration
HPE GreenLake
Best for Edge Computing Innovations

Although it’s a lesser-known cloud provider, HPE’s GreenLake cloud platform was one of the earliest pioneers in the edge computing realm, specifically with its Aruba tool. Some of Aruba’s key features include constant live monitoring, AIOps for service management, ITSM workflow automation, and expanded network utilization initiatives.
Aruba is offered as a monthly subscription cloud service with GreenLake, making it an easy tool to add or subtract as business priorities change, or as organizations begin experimenting with the edge.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- Open source database platform included
- Intelligent, workload-optimized storage
- Virtual desktop infrastructure (VDI)
- Point-and-click provisioning for private cloud development
- Aruba networking tool for edge infrastructure development
Adobe Cloud
Best Creative Software Cloud
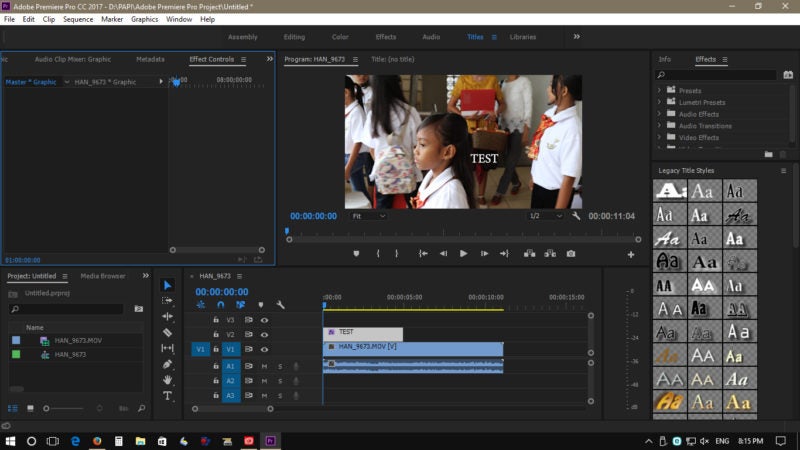
When Adobe originally transitioned its creative software suite to the cloud, many were unsure how successful it would be with this new subscription-based approach to creative tooling.
But Adobe has fared well and effectively cornered the creative cloud market, offering creative tools as individual applications and as the full-fledged Adobe Creative Suite via the subscription model. Because Adobe primarily offers SaaS solutions, it can and should be used in partnership with an additional infrastructure solution.
Cloud Category: SaaS
Key Features:
- Photoshop for image editing and design
- Premiere Pro for video editing and production
- Illustrator for vector graphics and illustration
- Adobe XD for web and other UX prototypes
- Acrobat Pro PDF tool
Cisco Cloud Solutions
Best Cybersecurity Portfolio
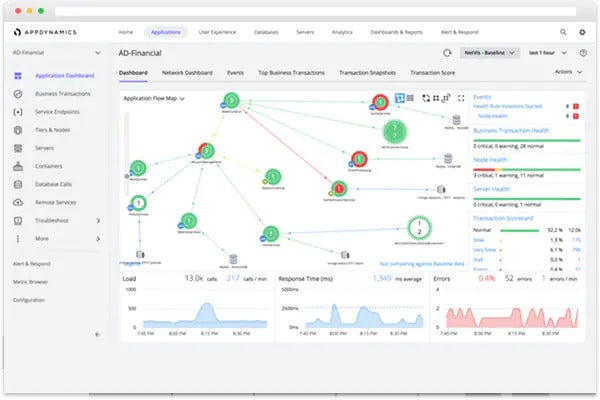
Cisco is best known for its collection of cybersecurity tools and services, and with Cisco Cloud Solutions, cloud customers get the best of both cloud and security worlds.
One of the core features that Cisco offers amongst its cloud tools is SecureX, a tool that connects the Cisco Security portfolio to the cloud and automates security initiatives across the infrastructure. Other key security features offered natively in Cisco’s cloud include Cloudlock, SASE, Stealthwatch Cloud, Tetration, and Umbrella.
Cloud Category: IaaS, PaaS, and SaaS
Key Features:
- AppDynamics performance monitoring
- Cisco Container Platform for container management
- Intersight dashboard and data visualizations
- SASE for secure access
- SecureX connection between cloud infrastructure and Cisco Secure portfolio
More on Cloud Technology: Biggest Challenges & Rewards of Enterprise SaaS
Key Features From Cloud Vendors
Data Analytics
With so many core enterprise applications hosted on the cloud, it’s important that the platform offers robust analytics and data visualizations to assess application performance. Look for platforms that offer easy-to-read dashboards and key analytics and monitoring metrics.
AI/ML
Artificial intelligence and machine learning are increasingly being added to cloud platforms, helping enterprise developers to test and deploy AI/ML tools on the cloud framework. As a bonus, many cloud platforms also offer AI/ML-powered security monitoring and automation features to users.
User Access Controls
Most enterprises need their cloud platform to be accessible to all employees, but different employees require different applications and different levels of access to sensitive data. Invest in a tool that provides advanced user access controls that sysadmins can update for different users and devices over time.
Security and Automation
Cloud providers, especially in the IaaS realm, typically double as cybersecurity providers, offering embedded or integrated applications that automate security monitoring across cloud infrastructure.
Scalable Storage
One of the core benefits of migrating enterprise assets to the cloud is the ability to scale tools and storage up and down as your company changes over time. Look at the baseline storage features your chosen platform offers, as well as the pay-as-you-go model offered for added storage.
Interoperability and Integrations
Especially for the cloud platforms that offer hybrid cloud or multicloud capabilities, it’s crucial that they offer interoperability and integrations with the key applications and tools your organization already uses.
Collaborative Workspaces
Because the cloud offers real-time updates and easy access for enterprise users, many cloud platforms offer collaborative workspaces and office suites where users can collaboratively update company assets.
More on AI and ML: AI vs Machine Learning: What Are Their Differences & Impacts?
Tips for Choosing a Cloud Vendor
Cost to Implement
The great thing about cloud solutions is that enterprise users can easily scale up or down with the tools they need. Really consider what tools make the most sense for your business and whether your preferred vendor offers those solutions, and at what cost. The top cloud providers tend to offer the highest costs for initial infrastructure and add-ons. But they also offer the widest portfolio of solutions.
Hybrid Cloud and Multicloud Flexibility
Not all cloud solutions are created equally when it comes to hybrid cloud and multicloud flexibility. When choosing a cloud vendor, ask yourself the following questions: Are they willing to assist with the transition from your legacy systems and data centers to their cloud? Do they offer solutions that allow you to keep and connect legacy systems to their products?
Cloud Application Library
Whether embedded or added via integrations, it’s important to consider which cloud vendors offer the most useful suite of cloud applications for your particular business line and use cases. The largest providers tend to offer very similar core products and solutions. But each of them offers different specialties, partnerships with outside vendors, and industry-specific solutions that could benefit your organization.
Cloud Security Features
The cloud makes it possible for your team and solutions to work in a more distributed environment. But as a result, security also needs to become more distributed to protect your global network. Does your chosen cloud vendor offer native cloud security, or do they partner with top cloud security providers? Do they offer a dashboard, analytics, and other helpful visuals so your internal team can stay on top of potential threats?
Other Key Features and Tips: Cloud Computing Market 2021
Who Needs Cloud Solutions?
The modern enterprise technology landscape is reaching a point where virtually every company uses cloud solutions of some fashion for their business, But if you’re still not certain whether cloud technology can benefit your business, consider investing in the cloud if you’re looking for:
- Simplified, remote access to company assets for employees
- Automated and distributed security solutions that can be easily monitored
- The ability to easily scale your storage and business applications
- Stronger disaster recovery and quality control features
- Easier access to emerging technologies, such as edge computing, AI, ML, and IoT
It’s likely that most workforces and enterprise projects will continue to operate in globally distributed locations. Although cloud computing companies and their solutions aren’t the only paths to successful management of a global enterprise, the cloud is quickly becoming the preferred method for uniting enterprise teams in an accessible, flexible, and secure environment.
Read Next: Top Edge Computing Companies for 2021
The post Top Cloud Computing Companies for 2021 appeared first on CIO Insight.
topDon’t Overlook IT Risk Compliance When Defending Against Cyberattacks
Posted in: Blogs, compliance, compliance audit, compliance risks, risk and compliance, Security - Sep 22, 2021With cyberattacks surging in recent months, company leaders from the C-suite to the boardroom are urgently asking: How can we best defend ourselves?
While it may not be the first thing that comes to mind, an essential piece of any effective cybersecurity strategy must be IT risk compliance. In fact, compliance and security should be viewed as one and the same — a fully integrated facet of your business operations.
For some, compliance is treated as a nuisance, or just another box to check. However, this somewhat complacent approach is exactly what can leave the door open for today’s sophisticated and aggressive hackers.
And as the government begins working more closely with businesses to regulate and strengthen security — take, for example, the new Joint Cyber Defense Collaborative — reaching and maintaining compliance is more important than ever to protect your organization and mitigate risk.
Read more: Top Cyber Security Threats to Organizations
Build an Integrated Compliance and Security Program
In order for companies to truly reduce risk, they need to have a security and compliance program that operates as one. This means breaking down silos and communication barriers, as well as integrating processes to ensure no risk falls through the cracks.
Because the truth is, “passing” a compliance audit does not provide absolute assurance a company has strong security controls, and having security controls in place does not mean they are operating effectively.
Having security controls in place does not mean they are operating effectively.
Instead, when compliance and security teams work together, IT risk compliance should be a natural outcome of information security best practices.
In practice, a truly integrated approach starts with an internal risk assessment to understand your vulnerabilities across the enterprise. Once this is completed, your security team can put in place controls — such as multi-factor authentication, risk-based access controls, and encryption — to protect information assets.
Then your compliance team can validate that those controls are functioning as planned and satisfy regulatory and industry frameworks. This process repeats as continuous risk monitoring continues to expose new and emerging risks.
In effect, the alliance between security and compliance ensures that controls are working. In the event of an attack, the company can have full confidence in the resolution and mitigation of risk.
Read more: Why Is Risk Management Important?
Establish Automated Processes for Better Collaboration
To enable better collaboration across security and compliance teams, automated workflows are a must. Implementing modern cybersecurity measures and assessing the compliance of those measures across a complex set of frameworks can be a time-consuming, manual process.
Many teams are still managing IT and information security compliance with manual processes and spreadsheets.
Yet many teams are still managing IT and information security compliance with manual processes and spreadsheets, leaving themselves vulnerable to errors, gaps, and risks. For these teams, automation can be a gamechanger. Automation enables true interoperability, improves lines of communication, and empowers teams to work together more seamlessly across first, second, and third lines.
Automation can be especially powerful for smaller teams, as it frees up time and resources to solve important business problems, better forecast risk, and decrease risk profile — the things that truly promote security.
Read more: Best Threat Intelligence Platforms & Tools for 2021
Create a Culture That Prioritizes Compliance
Risk is never truly isolated. If a compliance or security vulnerability is exploited, it affects your entire organization. That’s why it’s so important to create an organization-wide culture of compliance — from the board and the C-suite to internal auditors and security professionals.
When compliance comes from within an organization, rather than being imposed on employees, it becomes more than following the rules and doing the same old thing. It’s truly a part of the fabric of your culture, with each employee participating in protecting the company from cyber incidents.
As a business leader, it’s your job to create and foster this culture at every level, educating employees about the importance of risk and compliance. You must provide them with a practical framework to identify, manage, and remediate risks.
At the end of the day, cyberattacks are going to happen. It’s up to your company to have a strong, integrated compliance and security program in place, so when attacks do occur, it’s in your power to minimize their harm.
Read next: VPNs, Zero Trust Network Access, and the Evolution of Secure Remote Work
The post Don’t Overlook IT Risk Compliance When Defending Against Cyberattacks appeared first on CIO Insight.
topCX and UX: Similar, but Definitely Different
Posted in: Innovation - Sep 22, 2021Ask the average person if the customer experience and user experience are the same, and you will likely get either a tacit agreement or a confused shrug. This confusion can be directly linked to a common misconception that the two are essentially the same.
When you look under the hood of both customer experience (CX) and user experience (UX), then it’s crystal clear that they are similar, but different. Not only in what they are designed to do, but also how they behave as a business optimization strategy for end-user engagement.
To put it bluntly, companies aiming to deliver great products must understand both journeys to succeed.
UX Is How We Interact
According to ISO 9241-210, UX can be defined as “a person’s perceptions and responses that result from the use or anticipated use of a product, service, or product.” To put it into plain English, UX is how the end user interacts with the company, its services, and its products in a single channel — be that digital, print, or traditional media.
A great experience meets the customer’s exact needs with simplicity and elegance, giving the customer a feeling of satisfaction. On the flip side, this hides the requirement to understand what makes that experience great. And while the user interface (UI) is an integral part of the design, the UX is different from the UI.
A great experience meets the customer’s exact needs with simplicity and elegance.
Nielsen Norman Group (NN/G) explains this difference with an example of a movie review website. That website will have reviews, some good and some bad. Even if the UI for finding a film is perfect, the UX will be inadequate for people who want information about a minor independent release if the underlying database only contains movies from major studios.
To make things slightly more complicated, UX is often confused with usability. This popular misconception just muddies the waters. In fact, NN/G defines usability as a quality attribute of the UI, highlighting whether the system is easy to learn, efficient to use, pleasant, and so forth. With usability in the mix, total user experience becomes an even broader concept.
Read more: AI Equity in Business Technology: An Interview With Marshall Choy of SambaNova Systems
CX Is Where We Interact
So, if UX is about perceptions and emotions, then what is CX? The simple answer: CX is an umbrella concept that includes all the channels and products where a customer interacts with the brand, as well as how the customer feels about the brand.
For the most part, this is related to the cognitive, effective, sensory, and behavioral responses that occur along the various touchpoints in the product lifecycle. Companies usually measure these responses during what is known as the consumption process — the pre-purchase, consumption, and post-purchase stages, for instance.
CX is related to the cognitive, effective, sensory, and behavioral responses that occur in the product lifecycle.
All of these stages are directly linked to the cumulative impact on the customer over the course of these defined and multiple touchpoints.
For that reason alone, an organization seeking to optimize the users’ experience with their brands must focus on the CX design as a primary goal. The end-user experience typically is a journey with many touchpoints, so a good CX design team considers, assesses, and optimizes all those engagement opportunities.
CX refers to how users perceive a product, system, or service. From a company perspective, these can be slotted into customer service, advertising, brand reputation, sales process, pricing, and product delivery. That means there are defined goals to hit, mainly to dovetail business strategies with the actual customer’s overall experience — while always keeping the customer’s overall happiness in mind.
Read more: Best Practices for Plan-Build-Run Model
Critical Concepts, Different Outcomes
Although the terms “customer experience” and “user experience” have vastly different outcomes in terms of how the customer perceives and uses the product, there are multiple levels of engagement and customer interaction. Each of these is equally critical for the overall experience.
For instance, NN/G thinks about CX across three distinct levels: single interaction, journey, and relationship.
Interactions between a person and a brand can occur over a period of years (which, in some cases, might be a lifetime). So it becomes clear that you need to look at all aspects of that experience and how it impacts a person’s decision making. In today’s connected society, those interactions are considered to be primarily digital.
We should never forget that the bricks-and-mortar experience may have a direct impact on the virtual.
The single interaction level reflects the experience the person has using a single device to perform a specific task. This level is the one most commonly identified as the actual user experience and is not limited to digital interactions. Granted, most UX and CX is digital, but we should never forget that the bricks-and-mortar experience may have a direct impact on the virtual.
The journey level captures the person’s experience as they work to accomplish a goal (possibly using multiple interaction channels or devices to do so). In the vast majority of cases, this level is the end-to-end process of a customer completing their goal. In today’s connected society, this is the nirvana of omnichannel engagement.
The caveat is that delivering a first-rate journey-level experience is often tricky for companies, mainly because it requires significant effort to both integrate the various channels and coordinate different elements for interaction-level design.
Companies might experience a few unseen challenges, which include but are not limited to consistent messaging, omnichannel expectations, brand continuity, and the integration of a back end that can allow customers to move effectively between channels.
The relationship level refers to all the interactions between the person and the company throughout (no surprises here) the life of the customer relationship. Essentially, this is the complete customer experience level. At this point, brands focus on the customer’s actual (and potential) lifetime experience with the brand instead of a single interaction or a journey.
Read more: Hiring Crunch Hits IT
Improving the Experience by Working Together
As the goal of both is customer satisfaction, CX and UX must work together to deliver the best possible experience to the customer.
Companies will benefit when they understand how vital the relationship between CX and UX is to their overall success. Customers tend to pay more when they have a good relationship with a company with an amazing product. A recent Forrester report cites the fact that people are willing to pay up to 4.5 times more for a great customer experience than an average one.
People are willing to pay up to 4.5 times more for a great customer experience than an average one.
A good UX should improve overall CX. Aggregating customer feedback, for instance, can be leveraged to improve on the UX, since the brands can quickly improve product and customer experience based on the input from end users.
This becomes even more important when you consider that an experience might begin online and migrate to a physical engagement.
Why UX and CX Matter
With customer and user experience so important to brand reputation and customer loyalty, companies that fail to deliver either one, the other, or (in some cases) both, will experience pain points and a decline in their overall success.
A good CX enhances brand loyalty, but the UX must align with business optimization strategies. Importantly, the latter must deliver the subjective interactions that will influence the entire journey, and not just a single point in time.
And while CX is an umbrella under which companies can add both UX and UI, it is critical to understand that all three are equally crucial to the overall success of a product, system, or service. A happy user is a happy customer, and that is an emotional state that can be directly linked back to effective CX and UX.
Read next: AI Software Trends for 2021
The post CX and UX: Similar, but Definitely Different appeared first on CIO Insight.
topDaman News and Events
This showcases our company news and upcoming events. Please check back as this page will change frequently.


